At Def Con 24, I was given a chance to spend about an hour talking with the proposed CEO of MGT Capital Investments(NYSEMKT:MGT) outside of the Bally’s Poker Room. Joined by CTO Eric “Eijah” Anderson halfway through our interview, we discussed several important issues that I am simultaneously preparing to publish. It has been a month since I interviewed McAfee and Anderson but I have waited to release my interviews due to the controversy some believe have muddied the credibility of this company. Without specifically mentioning any of the detials, I will just share this tweet that I feel captures the spirit better than anything I could write.
https://twitter.com/ihazcandy/status/773876821267849217
Unfortunately even my editors at another site have decided to believe libelous claims from an avid troll, that I am on the payroll of MGT or one of its insiders. I feel that like others, they seem to be committed to their bias against McAfee and continue to judge this new company unfairly. On the other hand, by analyzing what John has been saying about the industry and not MGT, objective and free minded people may already understand the potential growth that his insight could bring. No matter how you feel about John McAfee, it is hard to deny the truth in his sentiment regarding the industry he helped to create.
John McAfee: Well when I started out people were saying ‘well virus aren’t a problem you’re insane’. Today I see the entire cybersecurity industry is operating on an outdated paradigm that is let’s find after the hacker gets in, let’s find the traces…”
As bold as the statement McAfee makes, it seems that the methods we use to secure our information are indeed outdated and is driving an increased demand for better cybersecurity. It is not hard to find indicators to support this idea.
At a time when global cybersecurity sales are expected to rise to $1 trillion by 2021, research is now showing that the problem of cyber-crime will cost companies $2 trillion by 2019. This reflects a widening gap between the efficiency of the solutions and the resourcefulness of the criminals.
In the United States, CNBC reported that the problem has become a drain on the infrastructure to the point that law enforcement agencies and hospitals have given in to ransomware demands for payment. There has also been a rise in reports that indicate that this type “pay or beware” strong-arming cost about 2,500 victims around $24 million in damages last year.
This year that number has already dramatically increased 500%. Recent data is also indicating that at the end of March 2016, Americans had paid over $209 million in order to regain access to their critical information. What I find most concerning about these figures is that those damages are limited to only the complaints reported to the FBI meaning that the actual costs of these crimes could be significantly more expensive.
What this shows that security professionals are as in the dark as law enforcement when it comes to protecting sensitive data. The problem is rooted in the lack of a solution that stops these intrusions while they occur
“JM: But by then it’s too late…He’s already in…
So obviously the paradigm doesn’t work.”
What Is Wrong With the State of Cybersecurity Today?
With a shift from Personal Computers to mobile devices, many hardware vendors have also moved to a cloud-based product offering secured by third-party cybersecurity vendors. With so many trusted names to protect the customer’s data, I believe if the paradigm is broken, then supporting data will be represented in the market. I feel the story of FireEye(NASDAQ:FEYE) and former McAfee CEO Bill DeWalt illustrates a great example of what John goes on to say is wrong with the current state of the cybersecurity industry.
Intel(NASDAQ:INTC) acquired McAfee’s former company after his departure in a $7.7 billion sale spearheaded by Bill DeWalt. Intel Security intended to embed features into its chipsets but now must consider selling its underfunded interest in cybersecurity under the McAfee brand. DeWalt would go on to leave to leave McAfee as a surge in venture capital funding poured into an industry and take the CEO role at the emerging FireEye venture in 2012. Under his leadership, their products took a proactive approach to developing anti-malware firewalls that brought a surge of interest in the company’s stock shortly after its IPO in early 2014.
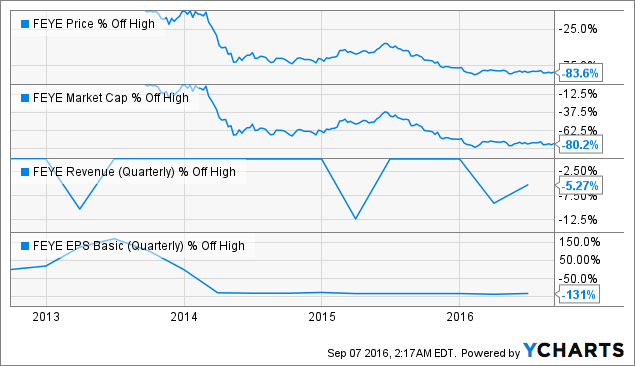
FEYE data by YCharts
With a flurry of new technologies to market interest from investors was on the rise yet the result of these new approaches was that from 2013 to 2015, the costs of cybercrime on businesses had quadrupled. In early 2014 FireEye had shed about 81% of its stock market value from its high of $13 billion and in the case of Bill DeWalt, he was recently replaced as CEO.
Eventually, the buzzword fueled hype had lost its effect on investors as the money pouring into the industry failed to produce tangible results. The Ponemon Institute released research that goes on to explain that the average cost of a data breach rose 23% in the last two years to $3.79 million. Like many other tech firms at the time, once these companies went from private ventures to public markets, investor confidence dropped as it became apparent that the current methods of information and network security were failing to keep up with enterprising criminals.
I feel that key players like Intel are discovering that they may have over-compartmentalized themselves as the disruptive effect of mobile technology shifts the focus of their business development. This tricky situation leaves Intel in a position to either increase spending by expanding the security operating expenses to competitive levels or sell the McAfee assets in order to focus on the company’s proposed move away from the PC market to a cloud-focused enterprise. Intel has released a manifesto that issued a proclamation that “The cloud is the most important trend shaping the future of the smart, connected world – and thus Intel’s future.“
As some companies may consider moving out of the crowded market, some have opted to consolidate. Investors have seen these effects manifest itself in the form of a more competitive industry and competitive acquisitions from established entities like Symantec(NASDAQ:SYMC) and its recent Blue Coat purchase.
Symantec who owns the popular Norton brand is paying $4.65 billion for the reported revenue of $598.3 million last year. All this for a company that decided to cash-in instead going through an IPO after it was acquired by Bain Capital last year for $2.4 billion. While Blue Coast has ceased to be a profitable business, those fundamentals did not stop it Symantec from paying a premium at x8 sales, after being turned away by FireEye earlier this year.
The Contrarian Case: Pillars of Disruptive Growth
It comes down to the concept of analyzing data of real-time user activity within a network, Gartner Research calls this, “Visibility”. It has become what Gartner refers to as its first pillar that describes the methods of analyzing a cloud-based security service as a means of both proactive security and a method to monetize the data being collected. Intel best summarizes Visibility with, “The many “things” that make up the PC Client business and the Internet of Things are made much more valuable by their connection to the cloud“
What if, instead of storing and sharing all of that user information, the company focused on developing real-world solutions to evolving problems? I believe that John McAfee’s re-entry is a calculated move to do just that. When you consider that on May 9th, 2016, MGT put out a press release marking his re-entry to the industry, weeks after Intel announced its new cloud-focused strategy.
JM:“…I spent 3 years finding the best products and that were in development out there and waiting for them to be ready and making both arrangements and relationships with the key people in this companies so that as for when they all matured they can use them.
Much like the investors funding the MGT reverse merger, McAfee is making a contrarian play on marketing the technology he has cultivated.
His security model of reducing risk by removing the needless connectivity of personal information through the cloud may grab the attention of those enterprises looking for an alternative. If MGT can offer a competitive solution to those organizations who are reluctant to move their most valuable information to the cloud the company’s recent acquisitions may prove to be a viable alternative platform to the cloud.
Although bearish investors may feel McAfee could be leading shareholders into the cybersecurity abyss of diminished returns, there is room for growth in the industry. With a potential market of over 85% of large enterprises switching to a cloud-based access solution, MGT is offering a packaged decentralized network structure to challenge the cloud’s projected dominance. The Ponemon institute finds that 87% of the data stored on the cloud is out of their company’s control. As more digital threats become newsworthy, businesses have shown that are uncomfortable keeping their most secure information outside of their control. 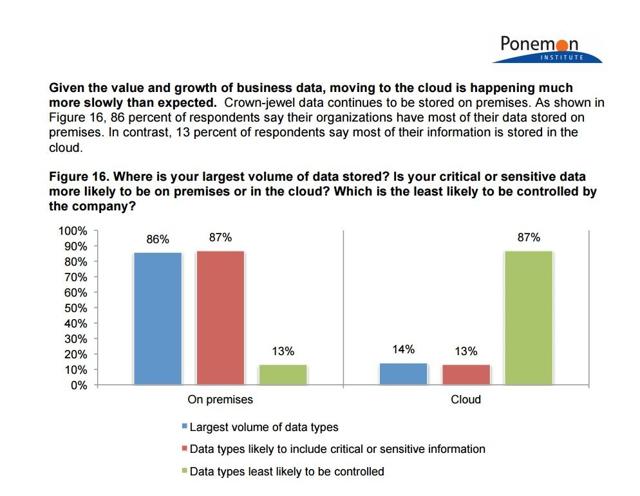
The recent acquisitions of Sentinel from Cyberdonix for 150,000 restricted shares of MGT stock, the company may find itself able to breach the moat of the global managed security services market that is projected to reach nearly $30 billion by 2020. I believe that MGT recognizes this potential market and is in a position to offer them on-site control of their data with a competitive advantage in some niche marketplaces. While the industry is extremely crowded, there is market research to support room for an alternative solution to cloud computing. If MGT’s offering can serve as an analog for Gartner’s four pillar approach as a Cloud Security Access Broker, then Sentinel MGT may prove to be wise acquisition for an initial product offering
For McAfee to expose shareholders to the growth projected in the industry, MGT will have to offer solutions to rival the likes of Symantec and FireEye. The real answer to the question of legitimacy for this venture will come from analyzing how well its technology can directly compete with hardware vendors like Cisco(NASDAQ:CSCO) and other established firewall providers as a real-time threat detection solution.
JM: For example, Sentinel… It doesn’t look for the damages that was done, and say “Ah-Ha! We have a problem.” It knows this within a matter for a second the first time a hacker attempts to approach the system.”
As lucrative as an opportunity this may seem, there is no guarantee that by purchasing a Next Generation Intrusion Protection Device like Sentinel, MGT can find customers who trust the minimalist approach. In order to provide the sales volume to ramp initial revenues, this product will have to offer is a new standard in real-time threat detection.
McAfee would go on to explain how he believes this has been achieved.
JM: A hacker doesn’t come in and dig up a bomb, he has to spend a lot searching.. First getting into the network…
Then it has to find where the thing I’m looking for is…
But we notice in the first few seconds his first approach
Our little box, it’s a passive box just watching, it uses a combination of heuristics and artificial intelligence and we notice instantly that this is an anomaly and there’s a packet or an intrusion here, right at that second that this shouldn’t be happening.
It then notifies our server, our server then does analysis…
All this happens in a matter of seconds.
At that point, you can take action which is close down that port and firewall or take remedial action which fixes the problem that let the hacker in.
Now isn’t that better than to wait for the hacker to come in and find the signs and say Aha there’s a piece of malware but good god that is months after he first came in…
It is a game changer it will change the entire face of cybersecurity in the way that companies address and reacts to intrusion.”
John McAfee, proposed CEO MGT 8/5/2016 Bally’s Poker Room, Las Vegas at Defcon 24
Sentinel and the Projected Growth of Enterprise Security
I expect that interest in Sentinel will grow in relation to the traditional IDS and IPS devices that have contributed to the slow response in threat-detection. With a low bar already set, all MGT may have to do is provide an actual solution to the problematic approach of analyzing data after the fact. According to FireEye, the median number of days that attackers are present on a victim’s network before being detected is 229. For this key reason, I feel that MGT has proven itself to be a legitimate contrarian play based on substantial market research that indicates Sentinel’s unique opportunity.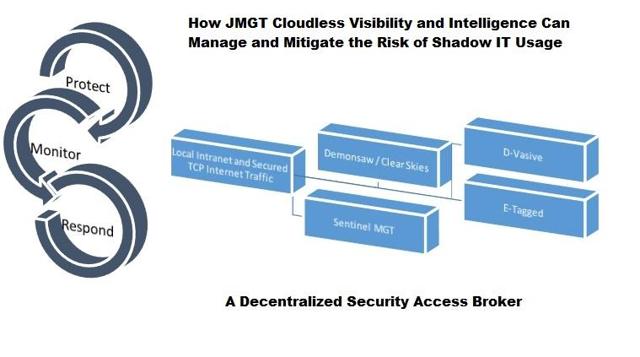
As the global enterprise governance, risk and compliance market continues to grow from to $11.5 billion by 2019, there will likely be customers reluctant to trust their information to devices that have underperformed. Where companies like Cisco and Microsoft offer IPS/IDS solutions, Sentinel was designed to be ideally suited for smaller areas compared to the standard 19-inch rack configuration that other vendors implement. Standard IPS and IDS solutions have several drawbacks other than their size. As McAfee explained, Sentinel acts as a passive box, meaning that it is on the other side of the firewall where the traditional IPS and IDS counterparts are located. This allows for Sentinel to reduce the risk of bottle-necking the network traffic. When a typical IPS/IDS solution has a malfunction or gets hacked, the entire network access point is compromised. I believe this to be an advantage over cloud solutions because of the obvious vulnerability of all data being transferred through one access point. 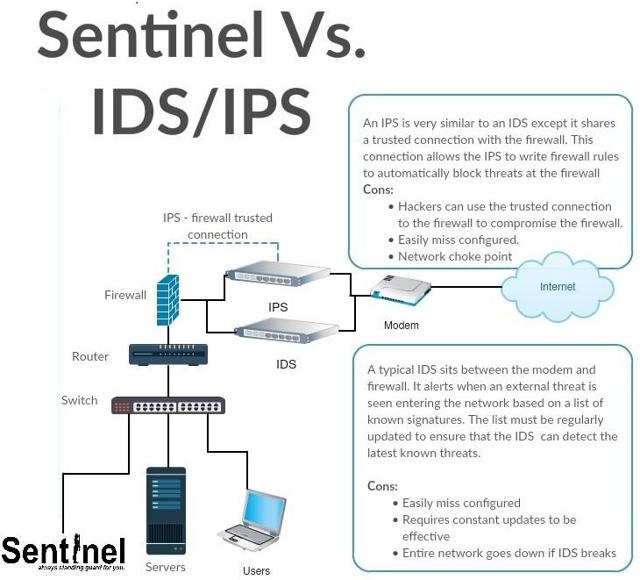
According to MGT’, Sentinel’s first production run is expected in Q4 2016 and gives investors exposure to the 13.2% CAGR projected for the market. The trend in information security spending indicates that by 2020, 60% of enterprise security budgets will be allocated for this type of rapid detection and response system and within two years 80% of these endpoint protection platforms will include similar A.I. and heuristic analysis similar to MGT. This may help the new company find some initial footing in the very rocky landscape that has become the cybersecurity industry. For now I will leave you with John’s proclamation to change the industry by bringing real-time results to problems that sometimes take years to understand.
In light of S.A. refusing to believe the simple truth, I am just citizen journalist using my free speech and free will to voice my opinion, I have decided to publish independently for now. I hope this rough notes will help you with your own due diligence. My research and writing is only made possible through your support. Thank you for taking the time to visit my personal website. Please use paypal to help support this blog.











You must be logged in to post a comment.